Technological advancements have introduced new vulnerabilities, making it essential for organizations to strengthen their defenses. Penetration testing is a proactive method to identify and fix security flaws ahead of potential attacks. This practice simulates cyberattacks to uncover weaknesses that could be exploited, thereby enhancing the overall security posture of an organization.
In this article, we will discuss the importance of penetration testing as part of a robust cybersecurity strategy. We will explore what penetration testing involves, the different types available, and how it fits into the broader context of maintaining strong security measures. Additionally, we will highlight the benefits of regular penetration testing, such as compliance with regulatory requirements, cost-effectiveness, and long-term investment in organizational security.
Understanding the critical role of penetration testing can help organizations prioritize their cybersecurity efforts, protect sensitive information, and build trust with stakeholders. Through thorough assessments and proactive measures, businesses can stay ahead of potential threats and ensure the resilience of their digital infrastructure.
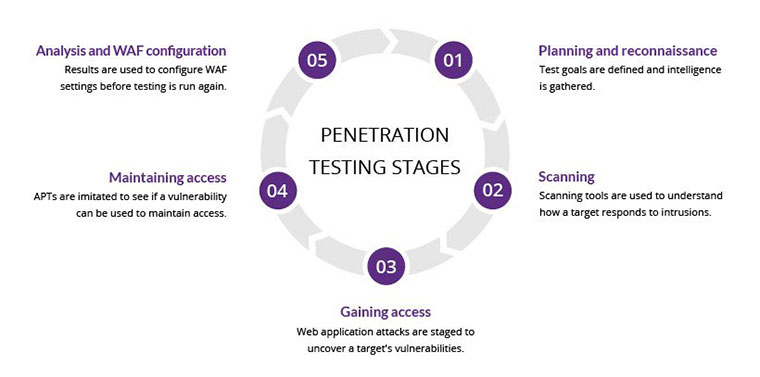
Understanding Penetration Testing
Penetration testing, often referred to as pen-testing, is a security assessment method where ethical hackers simulate cyberattacks on an organization’s systems. The primary goal is to uncover security vulnerabilities that could be exploited by attackers. By identifying these weaknesses proactively, organizations can take corrective actions before malicious actors can cause harm.
At its core, penetration testing aims to strengthen an organization’s security posture. It involves a thorough evaluation of the security measures in place, identifying gaps, and providing recommendations to mitigate risks. This preemptive approach is crucial in safeguarding sensitive data and ensuring the integrity of digital systems.
Different Types of Penetration Testing
Penetration testing can target various aspects of an organization’s infrastructure, each focusing on specific vulnerabilities:
- Network Service Testing: This type examines the security of network infrastructure, identifying weaknesses in network design, configuration, and implementation.
- Web Application Testing: Focuses on uncovering vulnerabilities within web applications, such as SQL injection, cross-site scripting (XSS), and other common exploits.
- Wireless Testing: Assesses the security of wireless networks, like Wi-Fi, ensuring they are properly configured and protected against unauthorized access.
- Social Engineering: Simulates attempts to manipulate individuals into divulging confidential information or performing actions that compromise security.
Importance of Proactive Testing
Effective risk mitigation requires proactive cybersecurity. Penetration testing services such as pentesting services reduce attacks on companies by surfacing and resolving vulnerabilities before attackers exploit them. This proactive approach protects sensitive data and systems and increases stakeholders’ confidence that the organization has strong cybersecurity measures.
Why Do a Pen Test?
Penetration testing utilizes automated tools and manual techniques to conduct in-depth security assessments. This blended methodology ensures that all potential weaknesses are thoroughly identified and addressed. By employing a comprehensive approach, organizations can enhance their overall security posture and mitigate various vulnerabilities across various systems.
Real-World Protection
Historical incidents such as the 2017 Equifax breach, which resulted in the exposure of sensitive information of 147 million individuals due to an unpatched vulnerability, highlight the critical need for regular penetration testing. Organizations can identify and mitigate risks by conducting routine testing before they escalate into significant security breaches. This proactive measure ensures that vulnerabilities are detected and resolved promptly, providing robust protection against real-world threats.
Enhanced Security Measures
Regular penetration testing is pivotal in maintaining and improving an organization’s security defenses. Continuous assessment and remediation of vulnerabilities ensure businesses stay ahead of potential threats. This proactive approach strengthens the organization’s defenses and demonstrates a strong commitment to safeguarding sensitive data and maintaining system integrity.
Regulatory Compliance and Legal Safeguards
Penetration testing is essential for complying with industry standards and regulations such as PCI DSS, HIPAA, and GDPR. Regular security assessments ensure organizations adhere to the required security practices, avoiding substantial fines and other legal repercussions. Organizations can protect their financial stability by meeting compliance requirements and maintaining trust with regulatory bodies and stakeholders.
Cost-Effectiveness and Return on Investment (ROI)
The penetration testing investment is cost-effective compared to the potential financial losses from a data breach. Preventing breaches through proactive testing helps organizations avoid expenses related to remediation, regulatory fines, legal fees, and lost business. While upfront costs may seem significant, the long-term savings and protection of financial resources and reputation make penetration testing a worthwhile investment.
Integration with Overall Security Strategy
A well-rounded security strategy involves multiple layers of defense, each complementing the others. Penetration testing plays a critical role in this layered security approach by uncovering vulnerabilities that may be overlooked by traditional security measures such as firewalls and intrusion detection systems. When combined with other security controls, penetration testing provides a holistic view of the organization’s security posture.
This layered approach ensures that any gaps or weaknesses are identified and addressed comprehensively. For instance, while firewalls and anti-virus software work to prevent unauthorized access and malware, penetration testing simulates real-world attacks to reveal deeper vulnerabilities. By integrating penetration testing into the overall security strategy, organizations can better position themselves to deter and respond to potential threats effectively.
Educating Stakeholders
One of the key aspects of integrating penetration testing into an organization’s security strategy is ensuring that key stakeholders, including senior management, understand its value. It’s crucial to convey that penetration testing is not just a one-time activity but an ongoing process that significantly contributes to the organization’s security posture.
Educating stakeholders involves demonstrating how regular penetration testing detects vulnerabilities before they can be exploited, thus mitigating risks to business continuity. By highlighting the proactive nature of penetration testing, its role in protecting sensitive business information, and ensuring compliance with regulatory requirements, stakeholders can appreciate its importance.
Properly informed stakeholders are more likely to allocate the necessary resources for penetration testing, recognizing it as an invaluable part of the organization’s cybersecurity framework. Regular updates and reports on the outcomes of penetration testing can further reinforce its relevance and benefits, ensuring sustained support from all levels of the organization.
Challenges and Considerations
Implementing a comprehensive penetration testing strategy comes with its challenges. Organizations may face budget constraints and difficulty in finding skilled personnel to conduct effective testing. To maximize the effectiveness of penetration testing within these constraints, organizations can prioritize identifying and testing their most critical assets and vulnerabilities.
Strategic planning is essential to allocate resources effectively toward the key areas of risk that pose the greatest threat to the organization’s security posture. Collaborating with trusted cybersecurity firms or utilizing automated testing tools can also help alleviate the impact of personnel shortages while still conducting thorough security assessments.
Future Trends and Innovations
The evolution of penetration testing is being accelerated by advancements in artificial intelligence (AI) and machine learning (ML). These technologies enable more efficient and effective testing processes by quickly identifying vulnerabilities and analyzing large volumes of data. AI and ML can simulate complex attack scenarios, enhancing the thoroughness of security assessments.
Automation is another emerging trend that facilitates continuous monitoring of security systems, adapting to new cyber threats as they arise. This constant approach ensures that organizations remain resilient against evolving threats and can respond proactively to potential vulnerabilities.
Conclusion
Overall, penetration testing services are essential for enhancing business security and resilience in the current cyber context. Applied regularly, these tests allow organizations to stay ahead of potential threats by identifying and mitigating vulnerabilities before they can be exploited. By investing in penetration testing, businesses are committed to maintaining strong defenses against cybersecurity threats, protecting sensitive data, defending their reputation, and building trust with customers and stakeholders.
Organizations should continuously reassess their cybersecurity stance and collaborate with penetration testing service providers for comprehensive assessments. In today’s digital world, cybersecurity is about protection, maintaining a trustworthy reputation, and ensuring business continuity.
Thomas Hyde
Related posts
Popular Articles
Best Linux Distros for Developers and Programmers as of 2025
Linux might not be the preferred operating system of most regular users, but it’s definitely the go-to choice for the majority of developers and programmers. While other operating systems can also get the job done pretty well, Linux is a more specialized OS that was…
How to Install Pip on Ubuntu Linux
If you are a fan of using Python programming language, you can make your life easier by using Python Pip. It is a package management utility that allows you to install and manage Python software packages easily. Ubuntu doesn’t come with pre-installed Pip, but here…











