Many companies switch to the server-side tracking model nowadays to boost their analytics and marketing efforts. The main reason for this is the better quality of tracked data and compliance with the privacy policies. These are standard points about which you can read all over the internet. However, you can hardly ever see any mentions about the importance of cybersecurity measures for server-side tracking. It is a huge miss, considering that all the tracked data is delivered to a server, and if it is not protected properly, a leak can happen at any moment. How to ensure that this does not happen, that your clients’ private information will not get stolen or sold to your competitors? We will discuss the most effective methods here.
Understanding the Security Risks of Server-side Tracking
When using the GTM server-to-server tracking approach, people usually focus on hosting the Google Tag Manager container on a cloud server and do not think about protecting it. This happens due to the lack of understanding of why it is important and what can happen to the data delivered there. We do not want to scare you in vain; instead, we want to inform you about what you should be aware of. Here are the most common reasons why you need to take care of the cybersecurity of your server and GTM container.
- MITM attack. A man-in-the-middle attack can also be called data interception. All the packages sent from the server to the analytical platforms can be intercepted if they are not properly protected or encrypted. This results in issues with data privacy regulations (as it is the server owner’s responsibility to guarantee data security), data integrity violations, etc.
- Unauthorized access. As server-side GTM handles the data in a more direct way, it becomes a piece of cake for cybercriminals of different types to seek out weak spots and vulnerabilities in the server’s configuration. If they gain access to the data, they can manipulate it and redirect it anywhere they want and need.
In both cases, the stolen or redirected data can be ultimately sold to third parties, spammers, or individuals who can use it to manipulate or harm the people it originally belonged to. If you implement server-side tracking for your company, it is your obligation to ensure that your client’s information is safe and sound on your server. We will give you a few hints on how to do so.
Securing your Server-side GTM Configuration
Things are not as complicated as they may seem at first glance. Several strategies allow you to ensure the safety of data on your server without hiring a cybersecurity specialist with a six-digit paycheck or spending years learning the matter yourself. A bit of time, a sprinkle of diligence, and a handful of tech proficiency – and you will be all set.
Implement HTTPS
HTTPS is one of the most basic and effective ways to ensure that the client→server→analytics data flow is not intercepted. While it does not give a 100% security guarantee (to be honest, nothing does), HTTPS encrypts all the data in transit, making it more difficult for hackers to intercept or steal it. It is crucial to use HTTPS for all types of sensitive data, for instance, payment or contact information.
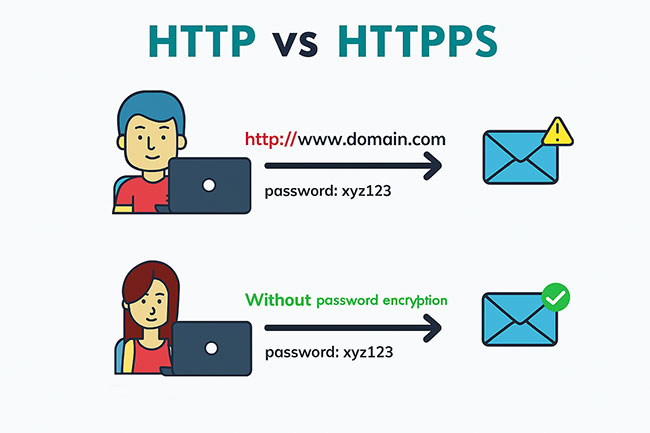
Implementing HTTPS for your server is quite simple and does not require much time or technical expertise. Basically, you need to obtain and configure the SSL/TLS certificate and then check whether all the requests to your server are made over HTTPS instead of the more common HTTP. It can be done in a couple of days over the internet. This is your first step in protecting the data on your server from hackers.
Stick to Strong Authentication and Authorization Practices
Server-side tracking is often associated with APIs, Gateways, and access to third-party services. What many people do not realize is that each of these things is a potential breach in your server’s protection layer. To ensure that these breaches are secured, implement strong protocols for authentication and authorization for all systems your server is linked with.
- API keys will mark your server’s requests to the external services. It may be compared to a password you say when arriving at another platform. If the password is wrong or non-existent, the request is blocked, and all the potential leaks become impossible.
- Create user groups and only provide the authorized users with access to server configuration and sensitive information (if necessary). It is also a great idea to implement SSO to decrease the risk of users forgetting or compromising their credentials.
- Multi-factor authentication will provide you with an additional layer of security. It will stop the hackers from accessing your server and GTM container even if the credentials were compromised.
If you stick to the recommendations we provide here, you will decrease the number of successful unauthorized login attempts to a minimum.
Use Tokens to Secure Private Data
Tokenization is a quite modern and elegant solution: instead of sending the actual data, you transfer a randomly generated token that possesses 0 value on its own. This system can be compared to the concept of money when valuable gold was substituted for paper. A token is completely useless for anyone who does not know what it stands for. In our case, only the server owner and the destination platform will be able to operate it, while anybody else will simply get a random piece of code should they intercept the data package.
Conclusion
If you come across any other ways to increase the security of your server GTM container, do not hesitate to implement them. No security is enough security; this is our honest opinion on the matter. The strategies and approaches we mentioned here are the initial cybersecurity steps everyone should take; if you still haven’t, we recommend you do so as soon as possible. And, of course, share with us your opinions on the matter and some hints and tricks you use yourself. We are happy to develop a cyber-secure community here! The strategies and approaches we mentioned here are the initial cybersecurity steps everyone should take; if you still haven’t, we recommend you do so as soon as possible. And, of course, share with us your opinions on the matter and some hints and tricks you use yourself. We are happy to develop a cyber-secure community here!
Thomas Hyde
Related posts
Popular Articles
Best Linux Distros for Developers and Programmers as of 2025
Linux might not be the preferred operating system of most regular users, but it’s definitely the go-to choice for the majority of developers and programmers. While other operating systems can also get the job done pretty well, Linux is a more specialized OS that was…
How to Install Pip on Ubuntu Linux
If you are a fan of using Python programming language, you can make your life easier by using Python Pip. It is a package management utility that allows you to install and manage Python software packages easily. Ubuntu doesn’t come with pre-installed Pip, but here…











