Timely threat detection is sacrosanct in cybersecurity management. Organizations cannot afford to drop the ball when it comes to maintaining the security of operations. That’s why real-time threat detection is indispensable for identifying anomalies and preventing them from infiltrating systems, networks, platforms, software, and hardware devices.
Any delays in detecting cybersecurity threats can have disastrous repercussions. If we ignore these threats, they invariably result in operational, financial, and reputational damage. It’s equally important to empower IT security teams with the right tools and resources. If we fail to plan, we plan to fail.
With AI-powered cyber-attacks on the rise, now is the time to put ironclad plans into operation. Businesses are in lockstep when it comes to maintaining the integrity of operations.
Tools Are Available to Stop Threats Dead in Their Tracks
Cyberattacks are complex in nature, design and infiltration capabilities. These invasive breach vectors routinely lurk undetected. By the time they are discovered, it’s often too late. They may have already compromised critical infrastructure and sensitive data.
That’s precisely why it’s essential for security architects, business executives and leadership to identify threats early. These threats include many potential dangers – Insider Risks, Zero Day vulnerabilities, malware, ransomware, and viruses. Each of them is serious enough to inflict heavy collateral damage. Fortunately, we can identify these threats early on and take corrective action before it’s too late.
Big problems invariably arise when threats are ignored or go undetected for too long. The truth is we simply don’t know how dangerous they are until systems shut down, data is compromised or the company shutters operations. It’s like playing Russian Roulette with your company’s health. That’s exactly why timely threat detection is a strategic imperative. Once a company adopts a zero-tolerance to threats, it can mitigate further damage.
A Proactive Posture for Operational Security
A proactive security posture can help to restore normalcy and maintain stakeholder trust. We should never forget that businesses do not operate in isolation; they are part of a global ecosystem. Security-conscious leaders praise a proactive monitoring approach, with advanced threat detection systems. This often includes behavioral analytics, AI-driven threat intelligence, and breakthrough security technologies like Checkmarx ASPM for AppSec teams.
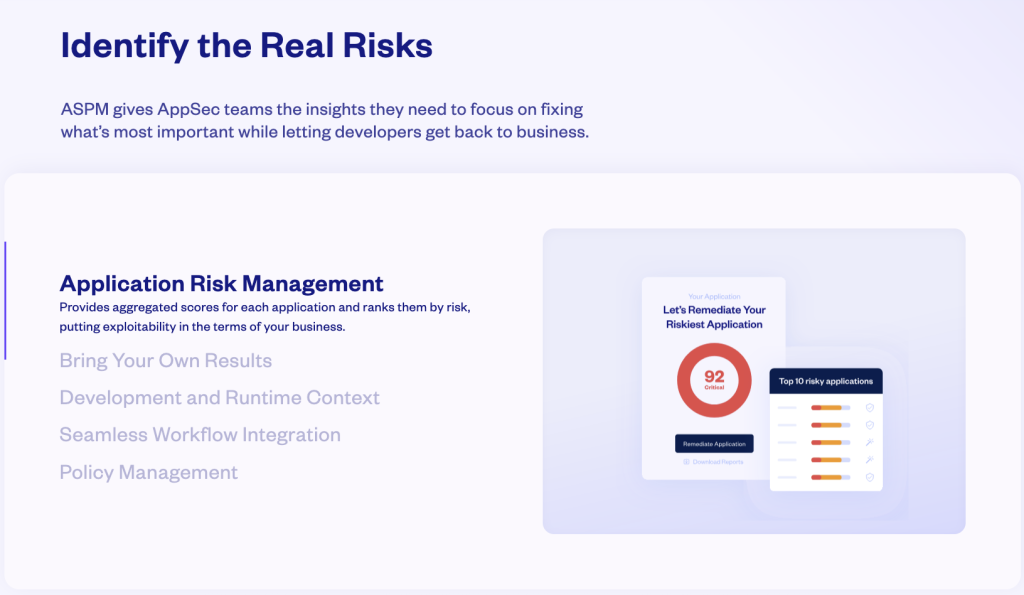
Application risk management tools deliver actionable insights, featuring aggregated risk scores across all applications running on the platform. Vulnerabilities are clearly identified and named, with corresponding risk levels assigned. Plus, these tools detail the source, nature, and current status of the threat. By providing easily actionable data, this safety system empowers IT security teams to prioritize remediation based on impact and urgency.
Consequences of Delayed Threat Response by Threat Vector
| Threat Vector | Potential Consequences | Supporting Data / Facts |
| Insider Threats | Data loss, operational disruption, IP theft, reputational harm | Careless employees and contractors may expose data via phishing clicks or shared credentials. |
| Viruses & Worms | Rapid system infection, network shutdown, data corruption | Worms replicate automatically; viruses remain dormant until triggered, infecting unpatched systems. |
| Botnets | Resource hijacking, DDoS attacks, credential theft, click fraud | Compromised IoT, servers, and devices are silently used to send spam or launch massive attacks. |
| Drive-by Downloads | Unseen malware installations, banking Trojans, exploit kits | Requires no user interaction -simply visiting an infected site triggers malicious downloads. |
| Phishing Attacks | Credential theft, malware infections, financial loss | Fake emails from trusted brands trick users into giving up sensitive info or downloading malware. |
| DDoS Attacks | Service outages, revenue loss, brand damage | Targeted systems are overloaded and crash; legitimate users are denied access. |
| Ransomware | System/data lockout, ransom payment, data loss | Encryption locks data; recovery may require full backups or expensive decryption, if available. |
| Exploit Kits | Vulnerability exploitation, malware deployment | DIY malware toolkits enable low-skill attackers to target unpatched systems. |
| Advanced Persistent Threats | Prolonged espionage, strategic data theft, regulatory exposure | APTs remain undetected for months, exfiltrating data silently. Avg. breach resolution time: 277 days. |
| Malvertising | Malware infection via ads, often on legitimate websites | Even high-profile sites (e.g., NYT, Spotify) have unknowingly hosted malicious ads. |
| General Impact (All Types) | Revenue loss, reputational damage, legal penalties, decreased productivity | 353M individuals affected in 2023 (US), across 3,205 events—78% increase year-over-year. |
| Delayed Containment | Increased breach costs | Breaches >200 days to contain cost $4.95M, 23% higher than faster containment. |
Threats move fast. Detection has to be faster. It’s not about chasing shadows. It’s about seeing the signals and acting early. The longer a threat lingers, the deeper the impact. That’s where application security tools come in: behavioral analytics, AI-driven threat intelligence, and ASPM for AppSec teams. Combined with endpoint monitoring and SIEM solutions, they help you cut through the noise. Cybersecurity isn’t just a technical fight. It’s a timing issue. Get it right, and you will stay ahead of the pack!
Alexandra Chen
Related posts
Popular Articles
Best Linux Distros for Developers and Programmers as of 2025
Linux might not be the preferred operating system of most regular users, but it’s definitely the go-to choice for the majority of developers and programmers. While other operating systems can also get the job done pretty well, Linux is a more specialized OS that was…
How to Install Pip on Ubuntu Linux
If you are a fan of using Python programming language, you can make your life easier by using Python Pip. It is a package management utility that allows you to install and manage Python software packages easily. Ubuntu doesn’t come with pre-installed Pip, but here…











